How to create an Entra ID Tenant
A nice quickstart or step-by-step guide wouldn’t be complete if I didn’t include the steps to create a new Entra ID tenant, right? Let me give you a high-level overview. Use the following steps to get started.
- First, browse the Azure Portal website – https://portal.azure.com/
- Make sure you’re in Microsoft Entra ID. You should be able to click it as one of the main icons at the top of the page.
- From the ‘Overview‘ screen, click the ‘Manage tenants‘ button on the top toolbar.
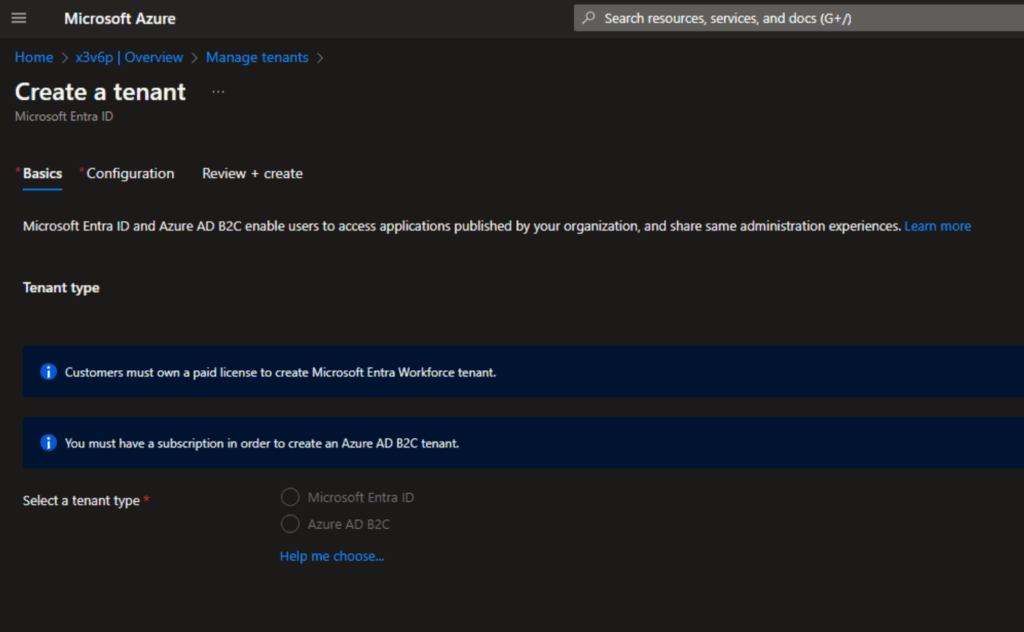
- On the Basics tab, click the ‘+ Create‘ button on the top toolbar.
- Here you can choose either ‘Microsoft Entra ID‘ or ‘Azure AD B2C‘. Choose Microsoft Entra ID and click Next.
- On the Configuration tab, enter an ‘Organization name‘, an ‘Initial Domain Name‘, and the geographic location.
- The Organization Name is simply a friendly description of your organization name.
- The Domain Name will be the initial domain name or prefix before the obligatory .onmicrosoft.com. You will probably want to come to this with a good number of ideas and permutations as MANY of these have already been chosen by other Microsoft customers.
- For the ‘Location‘, choose where you want your tenant to reside. The important point about the ‘Location‘ is that this needs to be thought out carefully. After you choose the geographic datacenter location of the tenant, you can NOT change it after the fact. Choose a location or leave ‘United States’ in the Country or region box.
- After you have the fields validated, click the ‘Create‘ button and you’re done.
Another quick note – when you create a new Microsoft Entra ID tenant, you become the first user of that tenant. This account is assigned the Global Administrator role. Be sure to validate this account and secure its password.
Choosing the best route when creating one
Above, I walked you through a specific scenario of tenant creation with Microsoft Entra ID. What I haven’t pointed out yet is that there are some different paths you can take, including the starting portal. I’d like to give you some explanation as to your choices, why it makes more sense to start in a specific portal, and why it makes sense to choose a specific top-level choice based on your intentions for the future. The type of users you’re managing, the type of tenant, and information security requirements are all criteria for how to proceed.
There are a few prerequisites or requirements you should be aware of before proceeding and planning. First, you will need an Azure account to start. Don’t worry if you’re only testing or managing development resources – you can easily create a free account to begin your testing. Also, if you’re not using an account with Global Administrator rights, you will at least need an account with the Tenant Creator role.
Choosing Microsoft Entra ID
When you start this process from the ‘traditional’ Azure Portal, your first choice will be choosing between Microsoft Entra ID or Azure AD B2C. You will want to choose the first, Microsoft Entra ID, if you intend to perform these functions:
- Manage access to your users and SaaS applications
- Scale up to millions of internal and external users
- Use the directory with Office 365, Aure, and other related Microsoft services and apps
- Configure Conditional Access policies to secure your users and applications, data, etc.
- Publish multitenant applications.
- This does allow you to incorporate ‘Azure AD B2C’ at a later time.
In case it’s not clear, this is the choice for managing all the aspects of user management – first name, last name, password, and other user settings.
Choosing Azure AD B2C
However, for that first decision, you will want to choose Azure AD B2C if you need to:
- Scale up to hundreds of millions of users
- Provide highly customizable sign-in and other identity management experiences for your customers, vendors, and partners as they access your external-facing applications.
- Remember – you will be unable to add ‘Microsoft Entra ID’ features/scope down the road with this option. Plan accordingly.
Special Note: Azure AD B2C cannot secure access to Office 365, Azure subscriptions, or other Microsoft services!
Can I add Azure AD B2C at a later time?
Yes, you certainly can. The vast majority of organizations will have existing tenants in Microsoft Entra ID (especially if you are utilizing Microsoft 365). Using ‘Azure AD B2C’ is as easy as accessing the administration controls in the Azure Portal.
Supporting Microsoft Work or School accounts, or personal accounts
If you are looking to build an environment for work or school accounts, or even personal Microsoft accounts (MSA), you can use an existing Microsoft Entra tenant or build a new one, especially for development purposes.
Many developers will already have a tenant through subscriptions or services they’ve previously purchased or trialed. To find out:
- Log in to the Microsoft Entra admin center as a Tenant Creator or Global Administrator.
- Check the upper-right corner and click your account info.
- You can confirm how many tenants you have access to verify if you can switch between them.
If you don’t have an existing tenant for your specific development purposes, go ahead and create a new one.
What’s the difference between an Azure subscription and an Entra ID tenant?
In summary, an Azure subscription contains your virtual resources in the cloud and the corresponding management interfaces. An Entra ID tenant is about identity and access management for your users, applications, and devices.
Here’s a table to help you understand the differences and how they are potentially related.
| Entra ID Tenant | Azure Subscription | |
|---|---|---|
| Definition | A dedicated and trusted instance of Entra ID that includes your users, groups, and applications. | Associated with an Azure Offer (free trial for example), contains your payment information, scale limits, and any administrative boundaries, and is the container for your Azure resources. |
| Association | Associated with a single identity (person, company, or organization) and can own one or several subscriptions. | Linked to a payment setup – each subscription will result in a separate bill. |
| Resources | Each of these tenants will have their unique users, groups, and applications separate from your other tenants. | In every subscription, you can add virtual resources (VM, storage, network, etc.). |
| Purpose | Identity and Access Management (IAM) | Resource usage and management. |
| Relationship with each other | Entra ID can have a 1:M relationship, but a Subscription can only trust one Entra ID tenant. | Subscriptions rely on this relationship with Entra ID to authenticate and authorize users, groups, applications, etc. |
Azure subscription vs Entra ID tenant